WordPress remains one of the most popular website platforms, and unfortunately, one of the most frequently targeted by hackers. Fortunately, with Softaculous WordPress Manager, you can significantly reduce your site’s risk using its built-in WordPress security features.
In this article, you’ll learn how to access WordPress Manager and apply powerful security configurations to harden your website without installing additional plugins.
Note: This feature is available from Softaculous version 5.9.2 and above.
How to Access Softaculous WordPress Manager
STEP 1: Log in to your cPanel.
There are three methods to log into your cPanel.
- Method 1: Log in to your cPanel directly.
- Method 2: Log in to your cPanel through your Customer Portal.
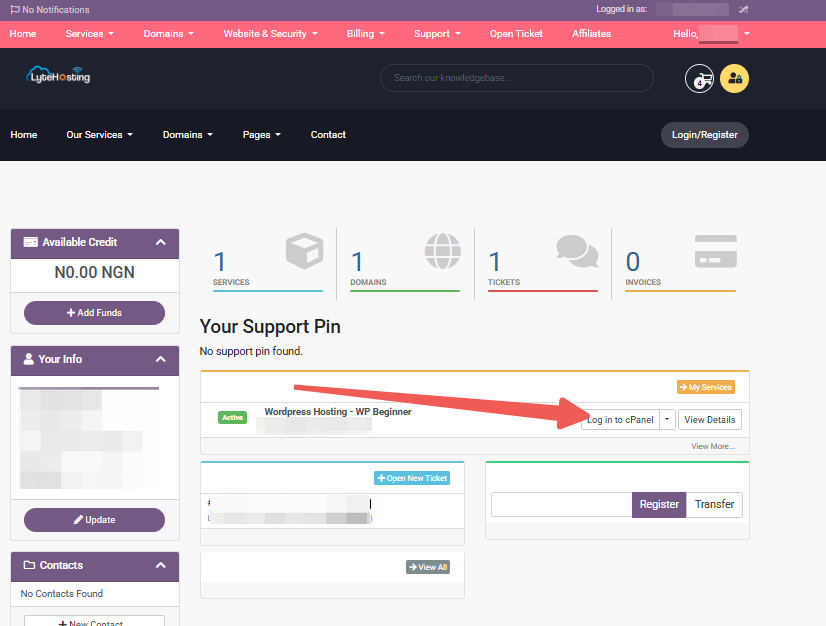
Through your Customer Portal;
- Log in to your Customer Portal.
- Click on "Log in to cPanel".
- Method 3: Log in using the details sent to your Email.
Through your Email;
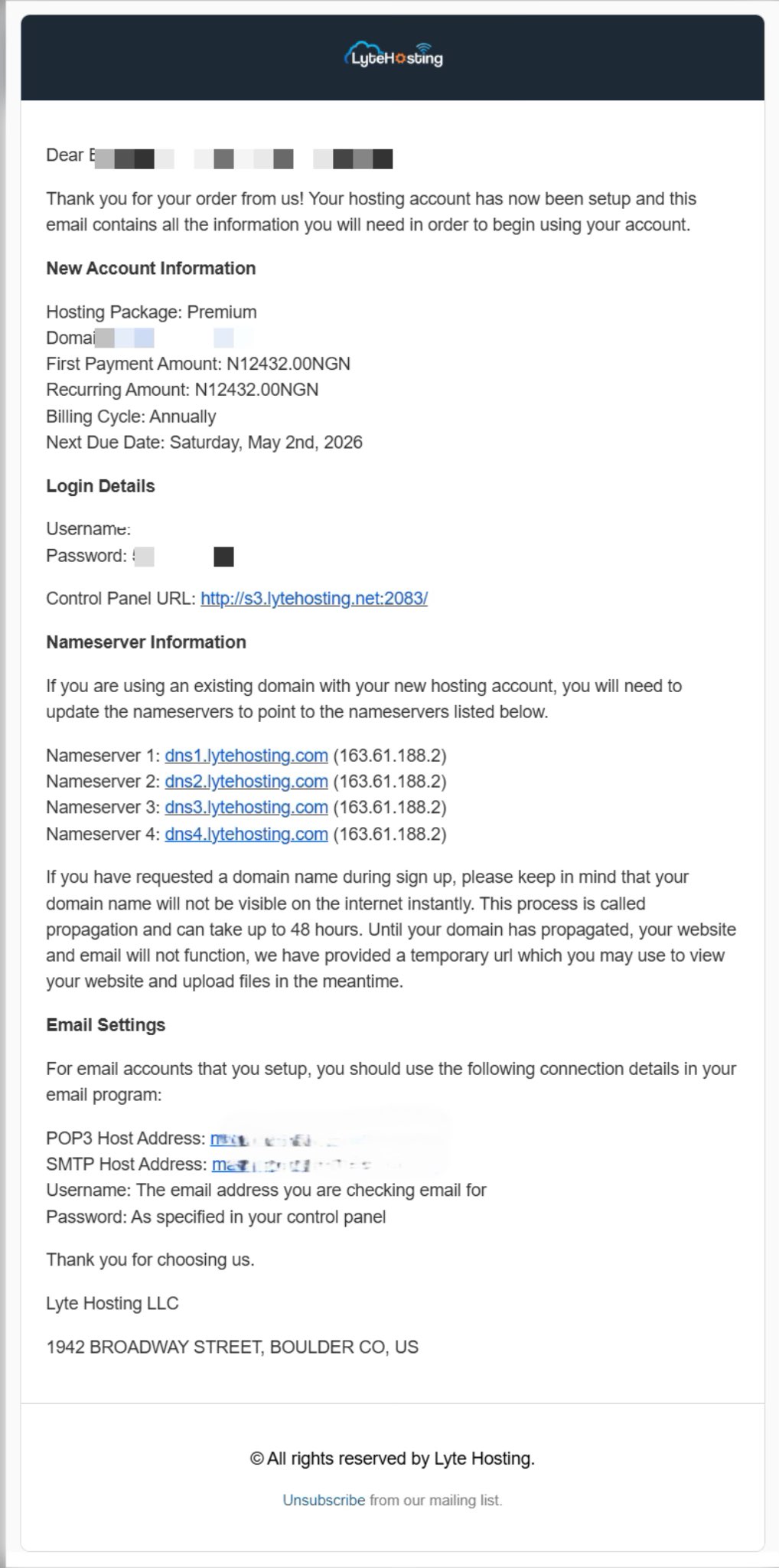
- When you purchase a hosting plan, your cPanel login details (including username, password, and cPanel URL) are automatically sent to your registered email address. Simply check your inbox (or spam folder), locate the email, and use the provided credentials to access your cPanel.
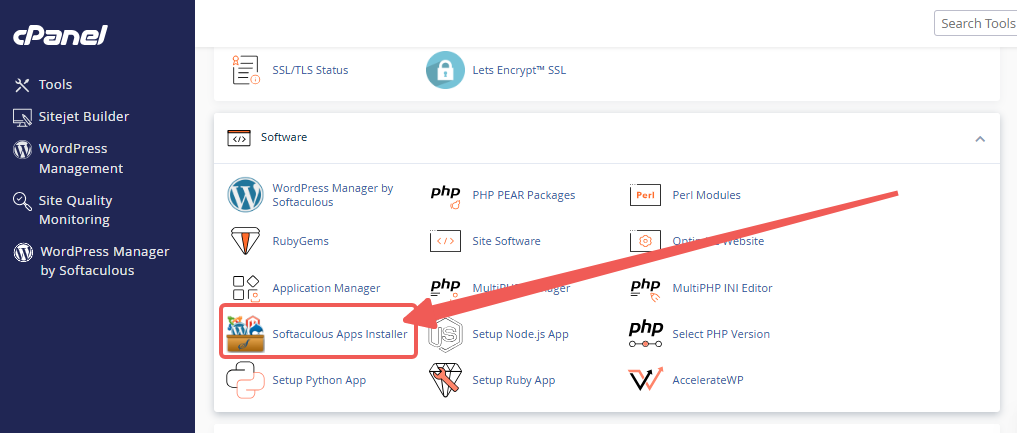
STEP 2: Locate the Software section and click on Softaculous Apps Installer.
STEP 3: Click the box for Installations.
An alternative is to select the “All Installations” icon from the menu in the upper-right corner.
![]()
STEP 4: Click the WordPress icon next to the installation you want to manage.
![]()
STEP 5: In WordPress Manager, select the website you want to secure.
STEP 6: Scroll to the Security Measures section.
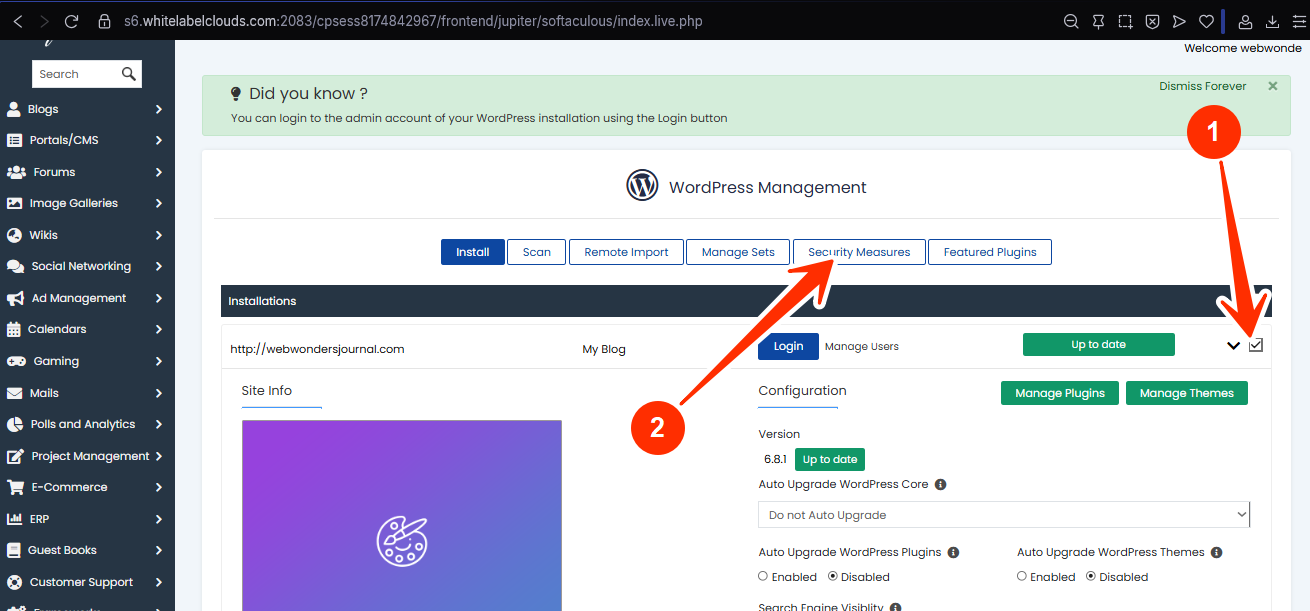
WordPress Security Settings in Softaculous
Softaculous WordPress Manager allows you to apply multiple security options to one or more websites simultaneously. Simply check the box next to each WordPress installation you want to protect and apply the selected measures.
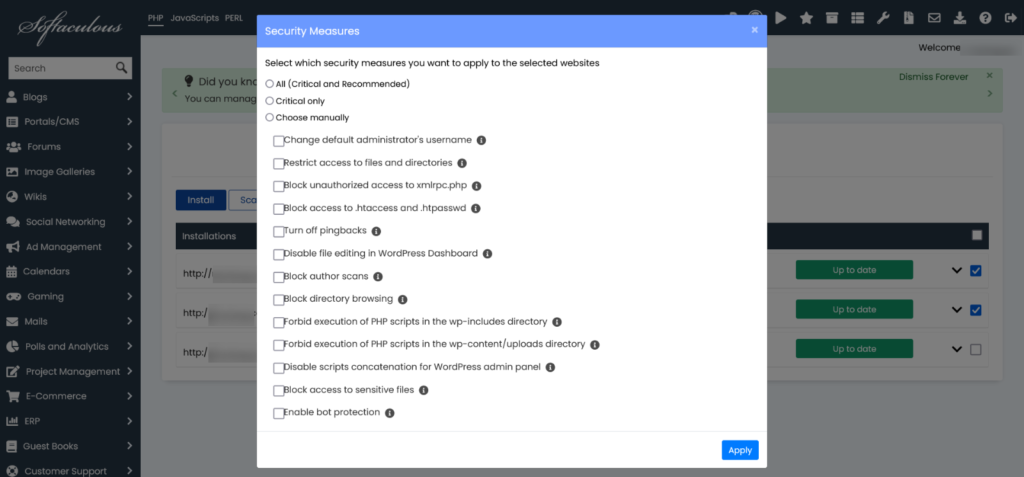
Here’s a breakdown of the available WordPress security options:
1. Change Default Administrator’s Username
If your site uses “admin” as the default username, it becomes an easy target for brute-force attacks. This feature lets you automatically replace the 'admin' username with a randomly generated one to prevent unauthorized logins.
2. Restrict Access to Files and Directories
Loose permissions can allow attackers to read or alter sensitive files. This setting secures file permissions:
- wp-config.php: set to 0600
- Other files: set to 0644
- Folders: set to 0755
3. Block Unauthorized Access to xmlrpc.php
Blocking this file helps prevent unauthorized login attempts and certain DDoS vulnerabilities.
Note: Custom .htaccess directives may override this setting.
4. Block Access to .htaccess and .htpasswd
Attackers gaining access to these files can exploit critical server settings. Enabling this option blocks public access to .htaccess and .htpasswd over the web.
5. Turn Off Pingbacks
Pingbacks are often abused to launch DDoS attacks on other sites using your WordPress installation. This option disables XML-RPC pingbacks sitewide and removes them from existing posts.
6. Disable File Editing in WordPress Dashboard
This setting disables the file editor inside the WordPress dashboard, helping prevent malicious code injections if a user account is ever compromised.
7. Block Author Scans
Hackers use author scans to detect usernames (especially admin accounts) and launch password-guessing attacks. This feature prevents those scans.
Note: Depending on your permalink structure, this may affect author archive pages.
8. Block Directory Browsing
Directory browsing allows outsiders to see the contents of folders on your site. If enabled, it exposes sensitive structure and file names. This setting disables it to protect your directory structure.
9. Forbid Execution of PHP Scripts in the wp-includes Directory
Malicious PHP scripts can be uploaded to the wp-includes directory. This feature disables execution of PHP files in this folder to prevent attacks.
Note: Custom .htaccess rules might override this protection.
10. Forbid Execution of PHP Scripts in the wp-content/uploads Directory
Your wp-content/uploads folder should only store media, not executable scripts. This setting blocks all PHP executions in this directory, a common target for attackers.
Note: As with other PHP-blocking rules, custom .htaccess directives may affect this.
11. Disable Script Concatenation for WordPress Admin Panel
Script concatenation can leave the WP Admin vulnerable to certain types of Denial of Service (DoS) attacks. Disabling it helps protect your admin interface, though it may slightly impact dashboard performance.
12. Block Access to Sensitive Files
This setting restricts access to core configuration or system files that may expose:
- Database credentials
- Server paths
- Software version details
Blocking access prevents attackers from gathering intel on your site.
13. Enable Bot Protection
Unwanted bots can flood your server with requests, slow down your site, or exploit known vulnerabilities. This feature blocks malicious or excessive bots, protecting your WordPress resources.
Note: Disable this temporarily if you're using a site scanner or vulnerability check tool, as it might block those bots too.
If you need help setting up any of these security features, our 24/7 support team is always available to assist you. Don't hesitate to reach out, we’re here to keep your website safe and running smoothly.




