What is the wp-includes Directory?
The wp-includes folder is one of the core directories in every WordPress installation. It contains essential files that power WordPress’s internal functions, such as formatting, media handling, and more.
But here’s the issue:
While these files are critical, they’re not meant to be directly accessed or executed by visitors. If left unprotected, attackers can:
- Upload malicious PHP scripts.
- Run custom commands from your server.
- Exploit known vulnerabilities in outdated WordPress versions.
Why Do You Need to Block PHP Execution in wp-includes
If a hacker gains access to your site and uploads a malicious PHP file into the wp-includes directory, they can execute commands remotely, inject malware, or create hidden backdoors to control your site indefinitely.
These files can sit quietly, often going undetected for weeks or months. During that time, your site may begin sending spam emails, redirecting users, or showing malware warnings, and you may not realize it until visitors start complaining or search engines blacklist your domain.
Blocking PHP execution in this directory prevents attackers from triggering these scripts, even if they manage to upload them.
How to Block PHP Execution in wp-includes Using WordPress Manager
STEP 1: Log in to your cPanel.
There are three methods to log into your cPanel.
- Method 1: Log in to your cPanel directly.
- Method 2: Log in to your cPanel through your Customer Portal.
Through your Customer Portal;
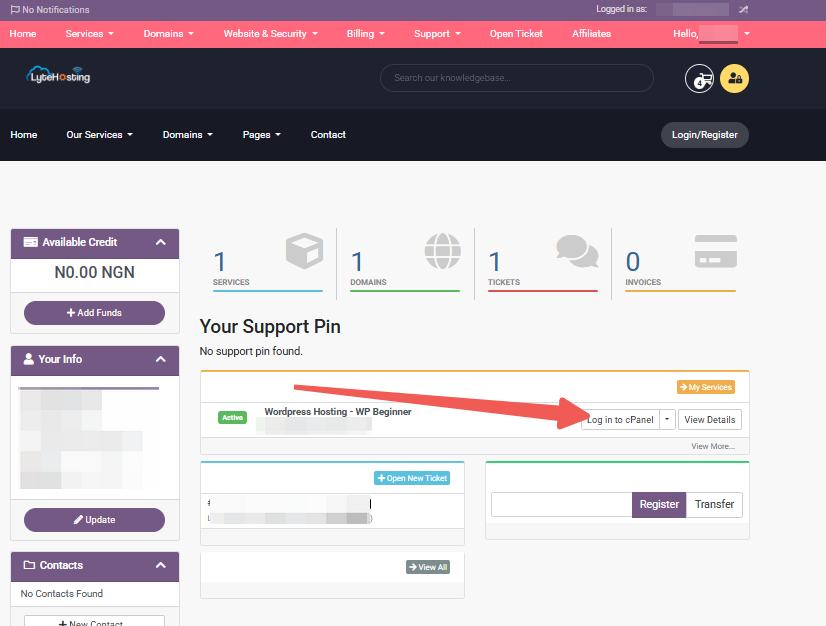
- Log in to your Customer Portal.
- Click on "Log in to cPanel".
- Method 3: Log in using the details sent to your Email.
Through your Email;
- When you purchase a hosting plan, your cPanel login details (including username, password, and cPanel URL) are automatically sent to your registered email address. Simply check your inbox (or spam folder), locate the email, and use the provided credentials to access your cPanel.
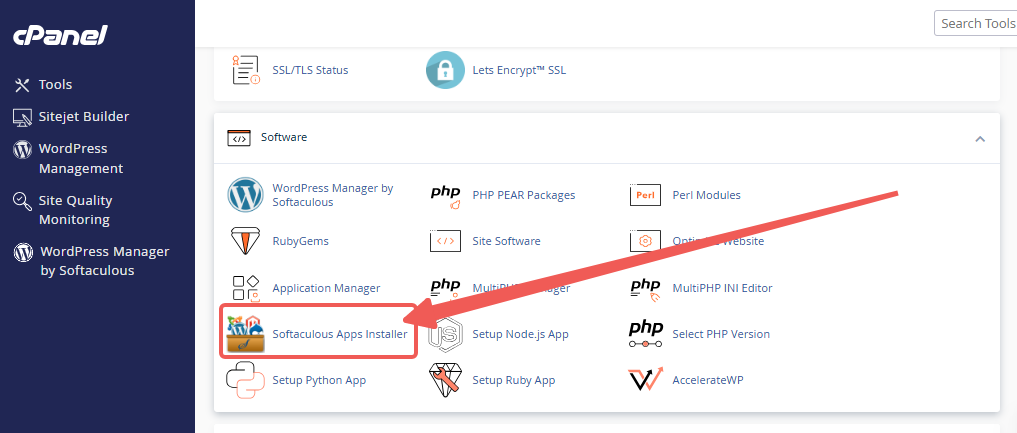
STEP 2: Locate the Software section and click on Softaculous Apps Installer.
STEP 3: Click the box for Installations.
An alternative is to select the “All Installations” icon from the menu in the upper-right corner.
![]()
STEP 4: Click the WordPress icon next to the installation you want to manage.
![]()
STEP 5: In WordPress Manager, select the website you want to secure.
STEP 6: Scroll to the Security Measures section.
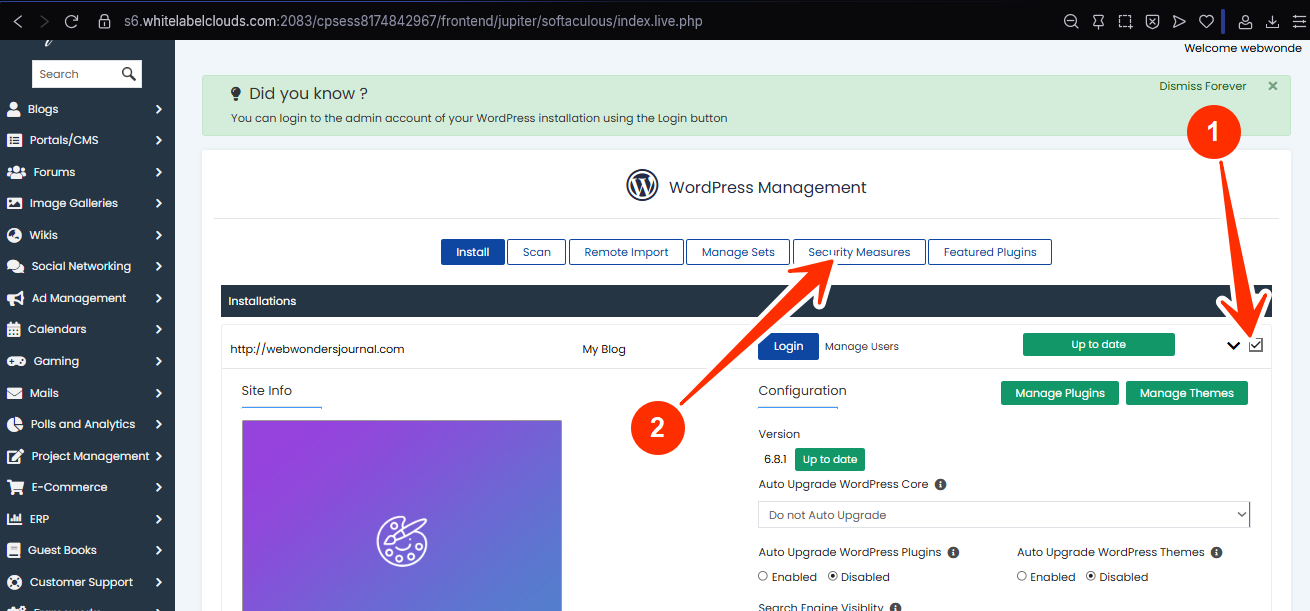
STEP 7: Checkmark the box for “Forbid execution of PHP scripts in the wp-includes directory”, and click Apply.
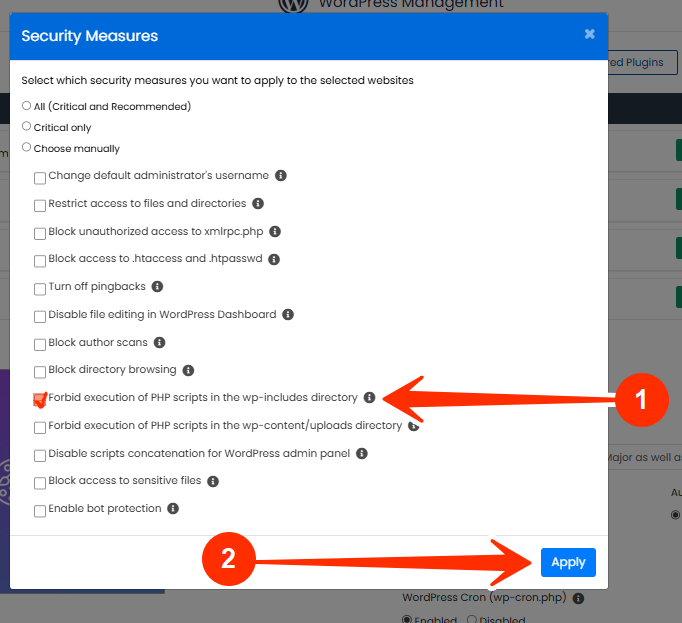
WordPress Manager injects the correct .htaccess rule into your root directory. This rule prevents any .php file inside wp-includes from being executed by an external request.
Frequently Asked Questions (FAQs)
Q: Will this affect my site’s performance or break features?
Not at all. These files are never meant to be accessed publicly — blocking them only improves your security without affecting user experience.
Q: Do I still need to keep WordPress updated?
Absolutely. This measure adds protection, but it doesn’t replace the need for core updates and strong login security.
Q: What if I accidentally allowed access before?
Apply the block now. Then scan your site using tools like Wordfence or Sucuri, or contact LyteHosting to run a deeper check for suspicious files.
If you need help, kindly reach out to LyteHosting support.




